Contact us
Our team would love to hear from you.

According to a report by Cybersecurity Ventures, global cybercrime is predicted to inflict financial damage of an estimated $9.5 trillion in 2024, rising to $10.5 trillion by 2025. Given the truly alarming nature of these figures, many enterprises are endeavoring to improve their cybersecurity postures by shifting from the traditional perimeter-based security model toward modern cybersecurity approaches. Whichever approach a company adopts for enhancing its cybersecurity, though, developing robust cybersecurity strategies, building multiple protection layers, and leveraging a significant number of digital tools, such as artificial intelligence (AI), will be required. In this article, we examine the fundamentals of AI in relation to cybersecurity, explore the power of this technology for fueling various cybersecurity applications, and unveil the challenges it poses and benefits it offers to the cybersecurity realm.

With its immense potential to revolutionize almost any vector of the global economy, AI can play a pivotal role in cybersecurity. What, though, does the concept of AI entail? Broadly speaking, AI is a branch of computer science and an innovative technology that focuses on building computer programs with the capability to simulate human intelligence and perform tasks that involve thinking, learning, and problem-solving skills. To create these intelligent programs, AI subsets, such as machine learning (ML), are used. By analyzing tremendous amounts of data and identifying any intricate underlying patterns, ML algorithms make it possible for computers to learn from these patterns, make precise predictions, and complete multiple tasks of varying levels of complexity.
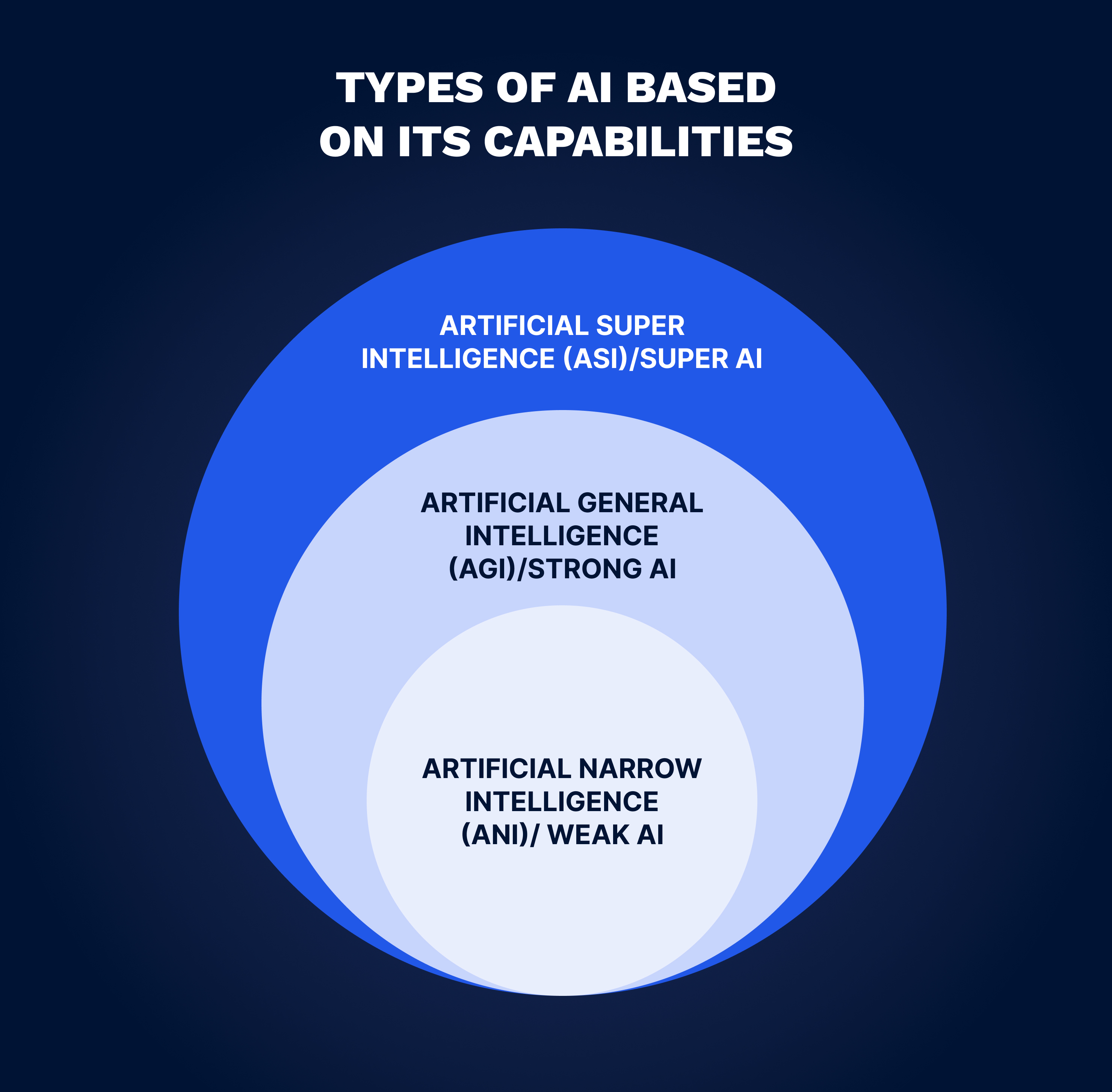
To fully understand the sophisticated role of AI in cybersecurity, it’s necessary to examine the different types of AI. Considering the capabilities of AI, it’s typically categorized into Artificial Narrow Intelligence (ANI), or weak AI, Artificial General Intelligence (AGI), otherwise known as strong AI, and Artificial Super Intelligence (ASI), or Super AI. The first type, weak AI, focuses on fulfilling a specific task in a narrow area and represents the actual state of the technology as it currently stands. Strong AI is a theoretical form of AI that refers to systems capable of completing a broad spectrum of high-level tasks across various domains, on a par with humans. Super AI refers to a level beyond strong AI, which would surpass the capacity of human abilities and intelligence through the creation of self-aware and ingenious machines. While strong AI and super AI are still considered science fiction concepts, weak AI has found numerous applications in a wide range of industries, with cybersecurity being no exception.
Having emerged in the second half of the twentieth century, the cybersecurity field has been drastically transformed in recent years, especially in the wake of the sophisticated and complex cyberthreats that have been powered by the digitalization process. To ensure the security of companies’ networks and systems and protect businesses from considerable financial losses, it has become necessary to capitalize on the synergy of high-performance digital tools and robust cybersecurity approaches. These approaches include the McCumber Cube, Zero Trust, and defense-in-depth (DiD), among others.
The McCumber Cube is a three-dimensional framework used to enhance information security within organizations through a focus on fundamental principles, such as confidentiality, integrity, and availability (CIA). Zero Trust is based on the assumption that users and devices within a network can’t be trusted and must be authenticated and authorized before accessing the network. Finally, DiD involves the creation of multiple security layers within a network infrastructure to ensure all-around protection of an organization’s data, digital assets, and systems.
To fully exploit the capabilities of these security models, combining them with AI is an absolute must. Below, we explore some of the ways in which cybersecurity professionals take advantage of AI in cybersecurity applications.
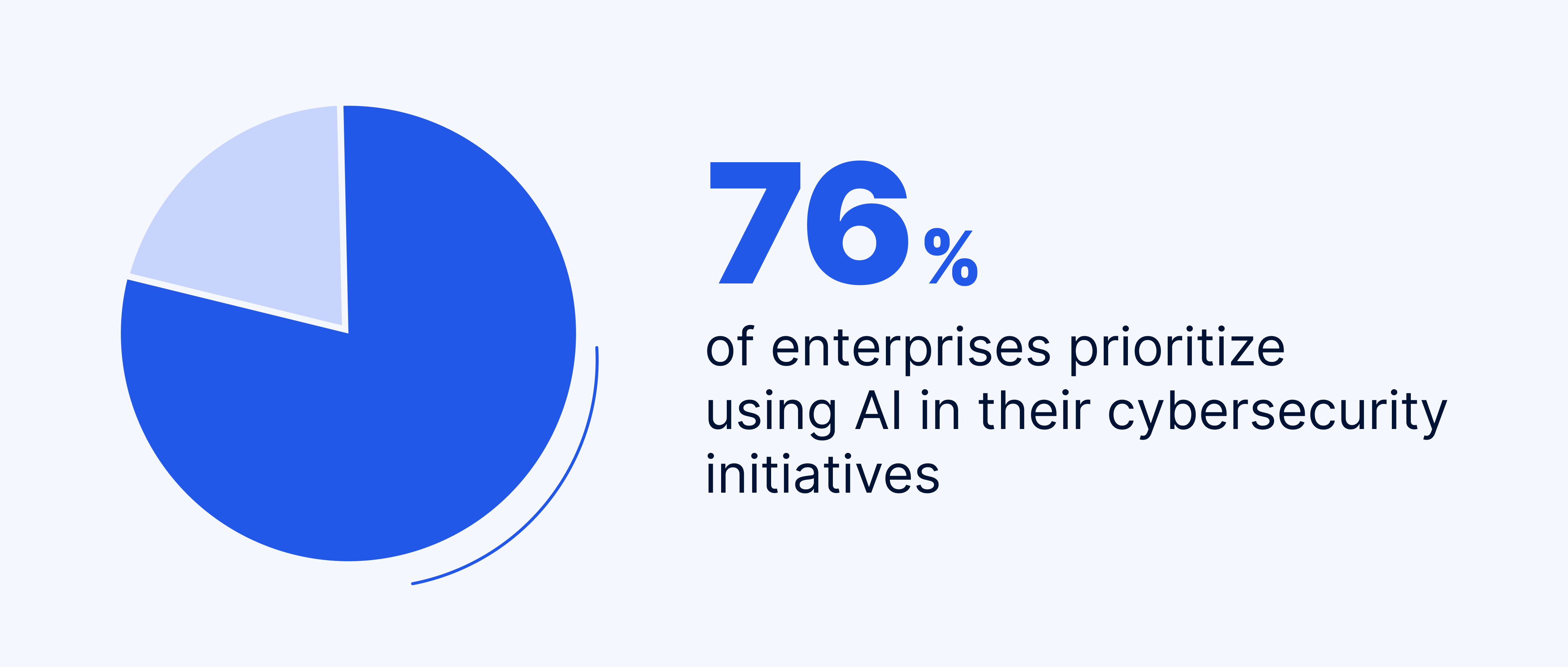
According to an analysis by Forbes, 76% of enterprises prioritize using AI for cybersecurity over other technological initiatives in their fight against cybercrime. The ways in which they do this are set out below.
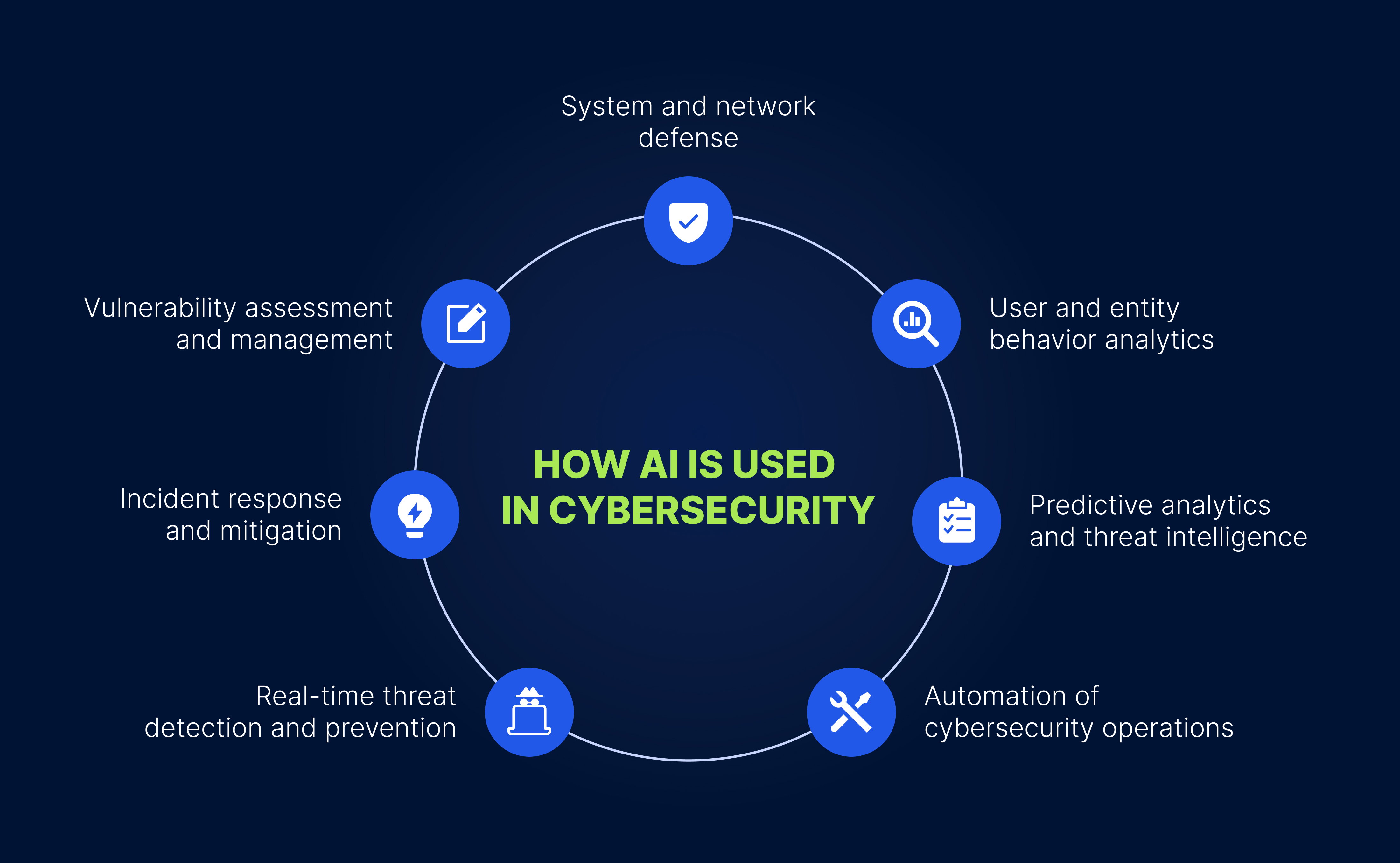
The primary reason why companies use AI and ML algorithms is to strengthen their system and network defense capabilities across a range of domains. Through a multitude of services, protocols, and tools, AI and ML bolster physical security, application security, and network hardening. Additionally, network segmentation, the hardening of wireless and mobile devices, and the enhancement of cybersecurity resilience are other applications of AI and ML in optimizing cybersecurity processes.
AI and ML algorithms offer organizations absolutely indispensable tools that can be leveraged to improve their defense mechanisms and automate multiple cybersecurity operations. Such operations include threat detection, threat hunting, vulnerability assessment, incident response management, continuous monitoring, and more. Automating security tasks significantly streamlines cybersecurity workflows, minimizes attack surfaces, considerably reduces response times, and offers a way of handling security issues with minimal risk. Overall, the automation of cybersecurity operations makes network security processes more efficient and less susceptible to human error.
Social engineering attacks, malware, man-in-the-middle (MitM) attacks, advanced persistent threats (APTs), distributed denial-of-service (DDoS) attacks, and password attacks are common issues that can potentially affect companies’ devices, networks, and systems. With the number of such incidents constantly increasing, organizations are integrating AI into their cybersecurity processes to detect both ongoing and potential threats and address these in real time. By analyzing extensive amounts of data from network traffic and system logs, as well as scrutinizing user behavior, AI and ML algorithms can help identify unusual patterns and anomalies, which in most cases indicate a cyberattack. After detecting a potential threat, the AI-powered system quickly flags it as suspicious activity, alerting security teams and enabling them to take immediate incident response measures. Such measures include blocking malicious activities, isolating damaged systems, and implementing security patches.
Cybersecurity experts capitalize on AI and ML for detecting internal threats by running user and entity behavior analytics (UEBA). Through the analysis of company data relating to the everyday activities of employees, customers, endpoint devices, routers, and servers, UEBA helps to distinguish suspicious patterns, detect anomalies, and identify malicious attacks. AI-powered UEBA swiftly triggers alerts, enabling organizations to effectively respond to a wide range of internal incidents, including insider threats, data theft, compromised accounts, and so on. Using AI and ML to drive UEBA helps organizations easily mitigate internal threats and safeguard the integrity of their digital infrastructures.
As cybercriminals continue to invent new and sophisticated methods in their attempts to hack into company networks, organizations need to ensure that their systems aren’t exposed to vulnerabilities, such as zero-day attacks. This is where AI solutions have proved their efficacy. By analyzing real-time data, including common vulnerabilities and exposures (CVEs), patch history, and exploit databases (ExploitDBs), AI and ML models learn to assess vulnerabilities and prioritize them according to their threat levels and potential impact. More importantly, security teams can leverage AI-based vulnerability management systems to implement remediation plans and establish efficient continuous monitoring processes to prevent new vulnerabilities from being exploited by threat actors.
Another use of artificial intelligence in cybersecurity extends to enabling predictive analytics of historical data and executing multiple threat intelligence activities. The goal of threat intelligence is to provide companies with evidence-based information about potential cyberattacks. With their ability to identify patterns, trends, and anomalies, AI and ML models assist cybersecurity professionals in understanding malicious agents’ attack behaviors, methods, motives, and possible targets. This proactive approach is highly beneficial. It offers companies an opportunity to bolster their defense capabilities by predicting the tactics, techniques, and procedures (TTPs) of threat actors. It can also anticipate various cyberthreats well before they occur.
In comparison to traditional security approaches, cybersecurity artificial intelligence is transforming incident management strategies by powering multiple proactive and reactive incident response and mitigation tools. Among these essential AI-driven instruments are stateless and stateful packet-filtering firewalls, application gateway firewalls, and next-gen firewalls (NGFWs). Other such tools include security orchestration, automation, and response (SOAR) platforms, and security information and event management (SIEM) systems. By integrating AI into incident response and mitigation tools, organizations can automate and refine their risk mitigation procedures and drive forward the accuracy, speed, and efficiency of their incident response processes. This is also a way of fostering continual improvements and adaptability in the rapidly evolving cyberthreat landscape.
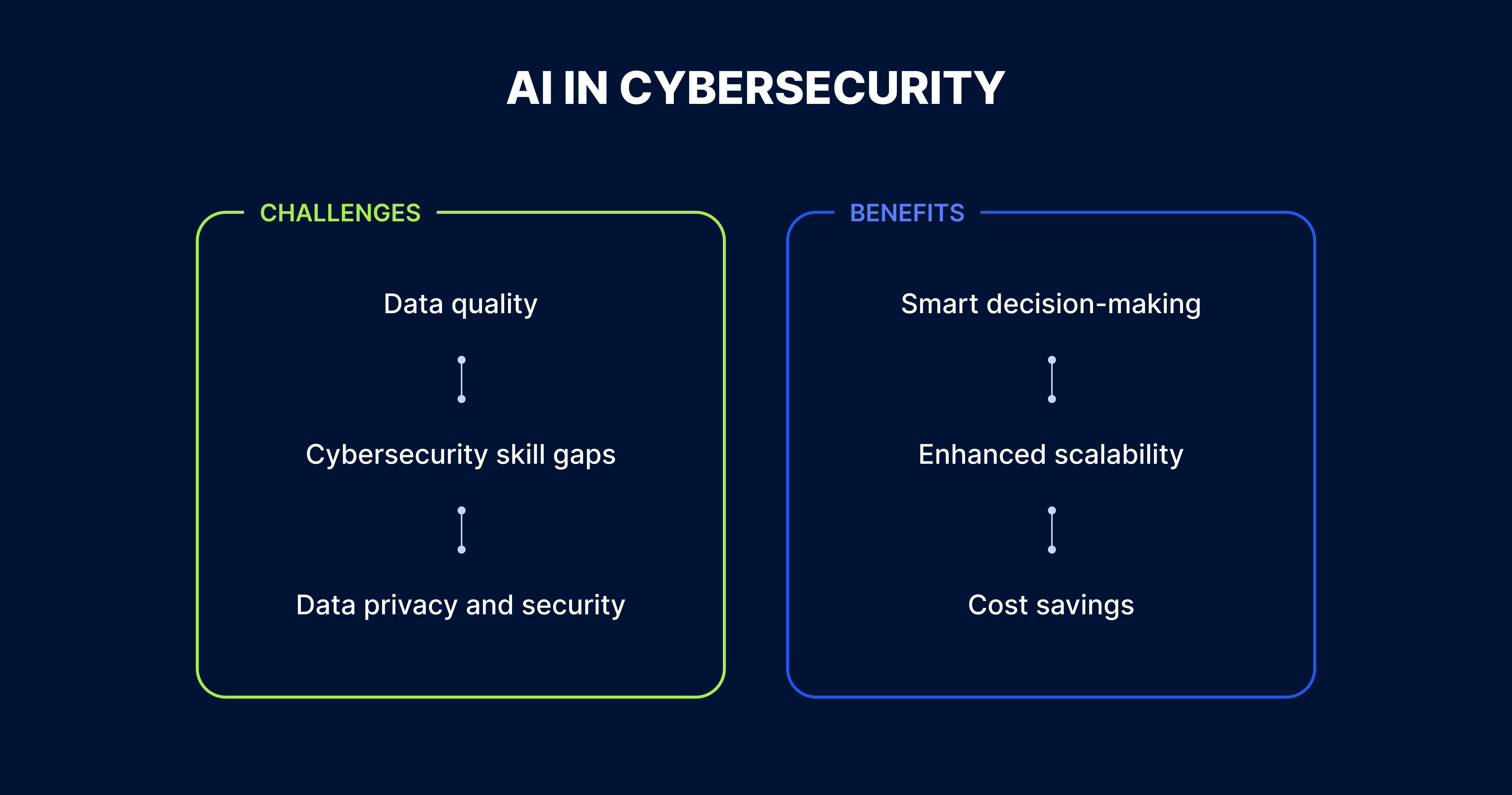
While AI cybersecurity solutions are poised to transform the way companies strengthen their defense capabilities, they nevertheless come with a few serious challenges. Understanding and promptly addressing these hurdles can help organizations unlock the full potential of AI and improve their cybersecurity postures. An overview of the key challenges involved in the implementation of AI into a company’s cybersecurity operations is provided below.
AI and ML models that have been trained using biased and intentionally manipulated datasets are liable to misinterpret data, and thus enable adversarial attacks, or deliver discriminatory and inaccurate results. Such outcomes have the power to significantly impact cybersecurity decision-making processes, leading to false positives and false negatives. While false positives mistakenly flag legitimate activities as potential attacks, false negatives fail in terms of detecting actual threats. To mitigate such risks, organizations should ensure the quality of their training data by meticulously curating and validating this before they initiate the training process.
Another challenge faced by organizations is a shortage of cybersecurity experts proficient in effectively integrating, managing, and maintaining AI systems. This can lead to poor resilience and inadequate defenses against cyberthreats. Providing training and upskilling opportunities for employees, fostering cross-functional collaboration, and promoting a continuous learning culture are some of the effective strategies that companies can implement to close their cybersecurity skill gaps.
Using extremely large datasets to train AI and ML models brings the risk of unintentionally exposing companies’ and individuals’ confidential data to privacy and security breaches. Apart from compromising the company’s defense integrity, such breaches may also result in financial and reputational losses and involve significant legal implications. To successfully address this particular challenge, ensuring robust data governance and compliance with privacy and security regulations is an absolute must.
Despite the complex challenges involved, capitalizing on AI in network security brings with it multiple advantages, as set out below.
AI and ML models possess the ability to seamlessly analyze and interpret extensive amounts of data in real time. They can also effectively detect anomalies and potential threats with high levels of precision. By providing a thorough understanding of their cybersecurity and compliance statuses, AI can empower companies to build, implement, and maintain solid cybersecurity strategies that are based on well-informed decisions. These strategies enable organizations to combine both reactive and proactive cybersecurity measures, and thus efficiently counter existing cyberattacks and mitigate emerging risks.
Improved scalability is another compelling benefit that AI offers to the cybersecurity field. Due to its prowess in handling large volumes of data from various sources simultaneously, organizations can use AI to easily expand their cybersecurity operations and adapt to rapidly evolving cybersecurity demands. This can be done without compromising data quality or the speed of data analytics. The AI-driven approach to cybersecurity not only helps organizations enhance their defense mechanisms in the face of potential cyberattacks but also strengthens the resilience and adaptability of their cybersecurity processes in the long run.
Although it requires upfront investment in infrastructure, artificial intelligence in cybersecurity offers the benefit of substantial cost savings in the long term. By empowering security teams to automate a wide range of repetitive tasks, AI provides an efficient means of mitigating potential risks and protecting companies from all sorts of cyberattacks. This leads to a reduction in operational costs and can also save organizations from substantial financial losses.
AI and cybersecurity tools, strategies, and techniques form an ideal synergy that can be used to safeguard companies’ digital frontiers. Despite still being in its evolutionary stage and yet to achieve the full potential of its abilities, AI offers countless opportunities to the cybersecurity industry. While integrating this technology into cybersecurity processes is associated with daunting challenges and seems impossible for multiple organizations, the advantages of harnessing the boundless potential of AI far outweigh the risks. If the fear of navigating the challenges of AI is what is stopping you from embracing it, don’t hesitate to reach out to our experts today! We will help you jump on the AI bandwagon and propel your cybersecurity operations to new heights!
Our team would love to hear from you.
Fill out the form to receive a consultation and explore how we can assist you and your business.
What happens next?