
Contact us
Our team would love to hear from you.

The pillar of successful business is a high-quality product. In software development, this means a reliable solution that meets all requirements and operates well. To meet these goals, it is necessary to perform quality assurance at every stage of development. An integral part of this process is penetration testing (pen testing), also known as ethical hacking, which evaluates the security of a system.
In pen testing, there are three fundamental methods that look at the software testing process from different perspectives: white box, gray box, and black box. In this article, we provide a detailed overview of black box pen testing, including the benefits, challenges, techniques, and steps of this approach.
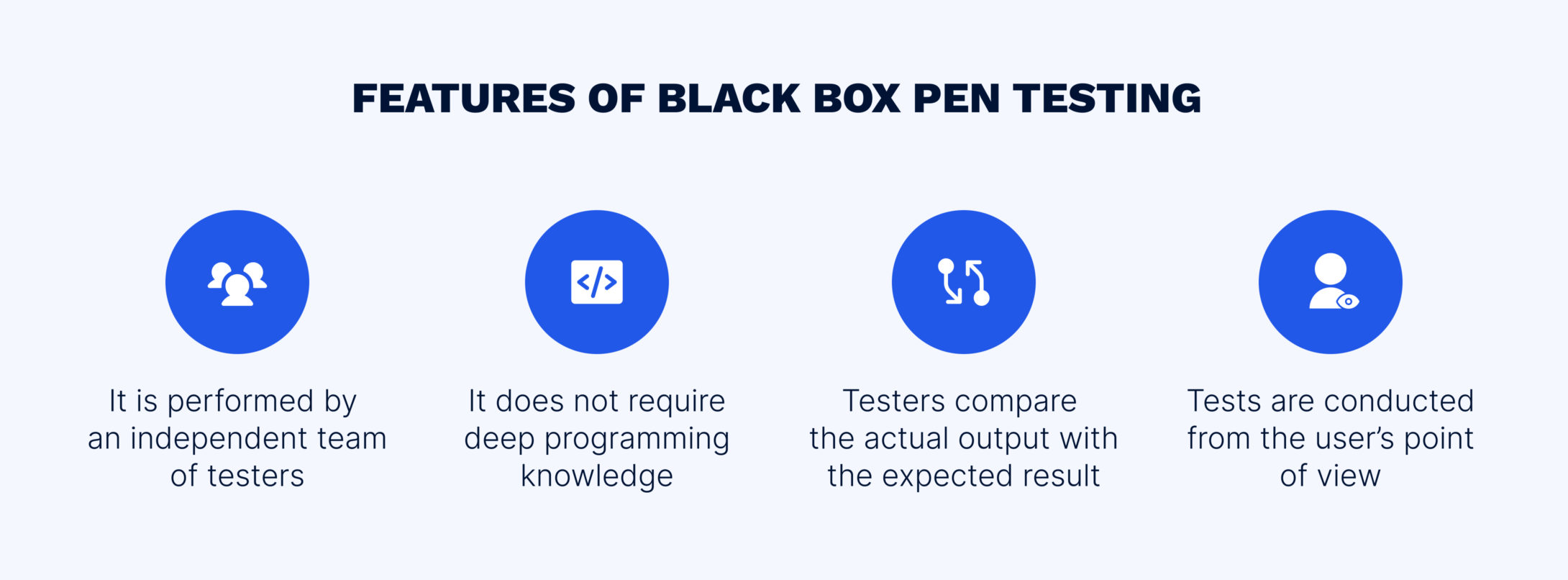
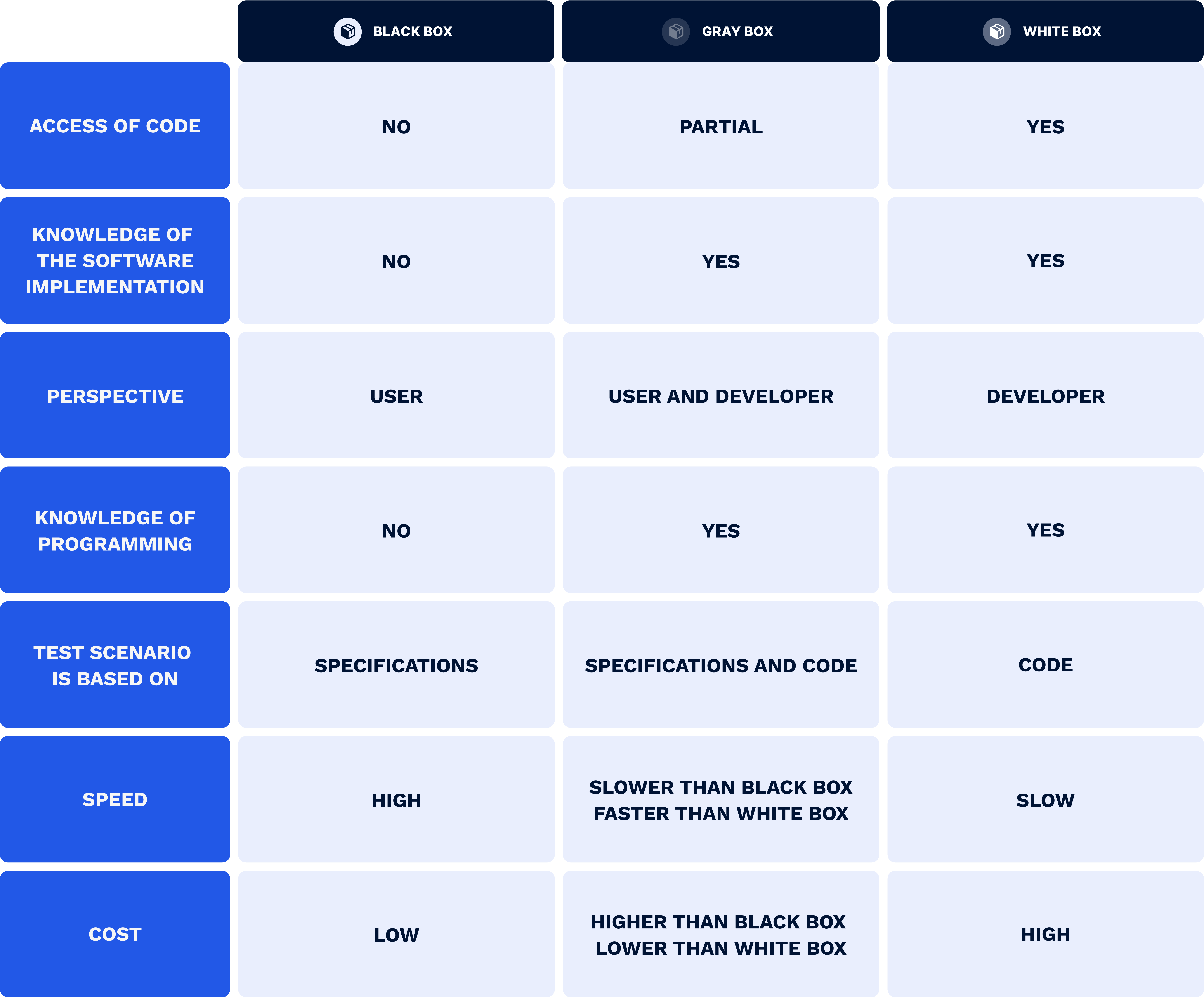
The concept of a black box is an object that produces valuable information without disclosing any data about its internal workings. In penetration testing, black box means examining software with an unknown internal structure while working with the external interfaces of the system. Simply put, a QA engineer does not have access to the source code and checks the system from the user interface.
In the black box penetration testing methodology, QA engineers act as hackers with no inside knowledge of the target system providing the most realistic scenario of how a criminal can attack valuable information.
All three types of pen testing have their own advantages in terms of the amount of information accessible to the tester.
White box (also known as glass box, clear box, transparent box, and structural testing) implies testing of the software’s internal structure. The core difference between black box and white box penetration testing is access to the code—with the white box strategy, the QA expert has full knowledge of all elements of the system.
The focus is on verifying the input and output data flow, improving the design and usability, and enhancing security. To identify potential points of weakness, QA engineers sift through a large amount of data available, which makes this type of pen testing the most time-consuming. Furthermore, although white box pen testing provides a holistic assessment of both internal and external vulnerabilities, the high level of system knowledge may negatively affect testers’ behavior as they operate using information beyond the reach of hackers.
This is a combination of white box and black box. Gray box testing requires incomplete knowledge of the internal processes. In other words, the code is known or used only partially. Having access to the internal structure and algorithms of the software, testers can write more effective test cases while the testing itself is performed from the user’s perspective.
In addition to the “hacker’s mind”, black box pen testing offers the following advantages:
Black box can be performed to test various aspects of a system or application, including:
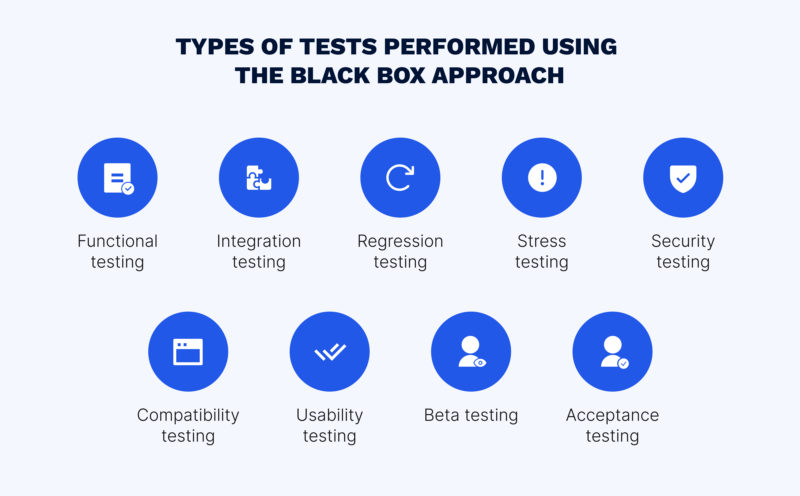
Functional testing. Experts check whether all features behave as declared in the requirements.
Integration testing. Testers check whether all components of the system work correctly as a whole. Regression testing. Specialists ensure that the new code does not lead to errors in the previous functionality.
Stress testing. QA engineers deliberately overload the program to evaluate the system performance under extreme conditions.
Security testing. Our black-box security testing experts test the software to evaluate security and identify any vulnerabilities that could be exploited by an attacker.
Compatibility testing. Testers check if the software or system is compatible with different operating systems, browsers, and devices.
Usability testing. QA specialists test the product from the standpoint of ease of use.
Beta testing. Testers evaluate a nearly finished product in the user’s shoes.
Acceptance testing. Checked by experts, the product is sent to the client, who verifies whether or not the software meets the requirements.
To detect all errors in a program, it is necessary to test all possible data sets. To do this, the black box strategy employs different techniques.
The essence of this method is to split the input data into groups and test only one sample from each. For example, if the site registration is available to individuals over 18, QA specialists can test only one date of birth in the “under 18” group and one date in the “over 18” group to see if the restriction works.
The technique is very close to the ECP method. BVA involves evaluating the ends or boundaries of input values. For example, a field accepts only numbers from 0 to 9. The testers can use the numbers -1, 5, and 10 to ensure that the input data is checked correctly.
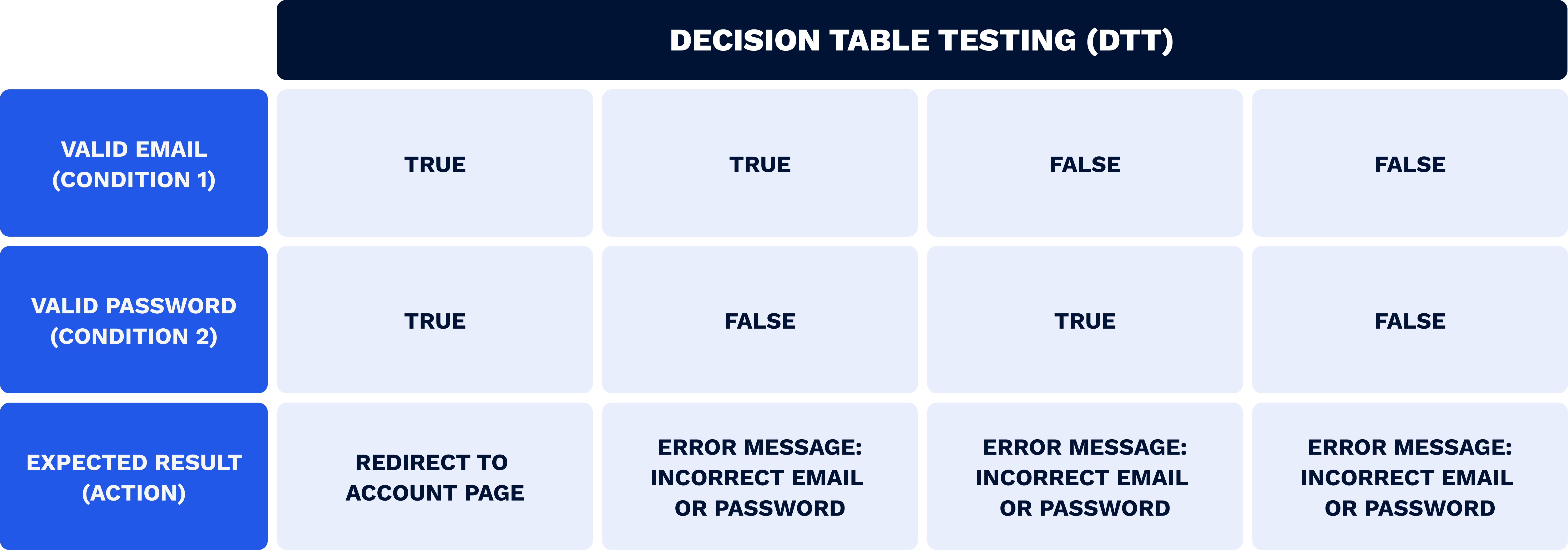
This technique is used to visualize multiple combinations of inputs. In the table, testers insert the variables and the outcomes. Such a method allows QA engineers to summarize all the results of a situation in a convenient and сoncise way.
As the name implies, this method consists of guessing the most frequent bugs. This technique is based on the tester’s proficiency, and therefore, requires extensive experience in the domain. EG does not follow any specific rules and can be used for checking common errors, such as dividing by zero, entering spaces in text fields, pressing the submit button without entering input values, and others.
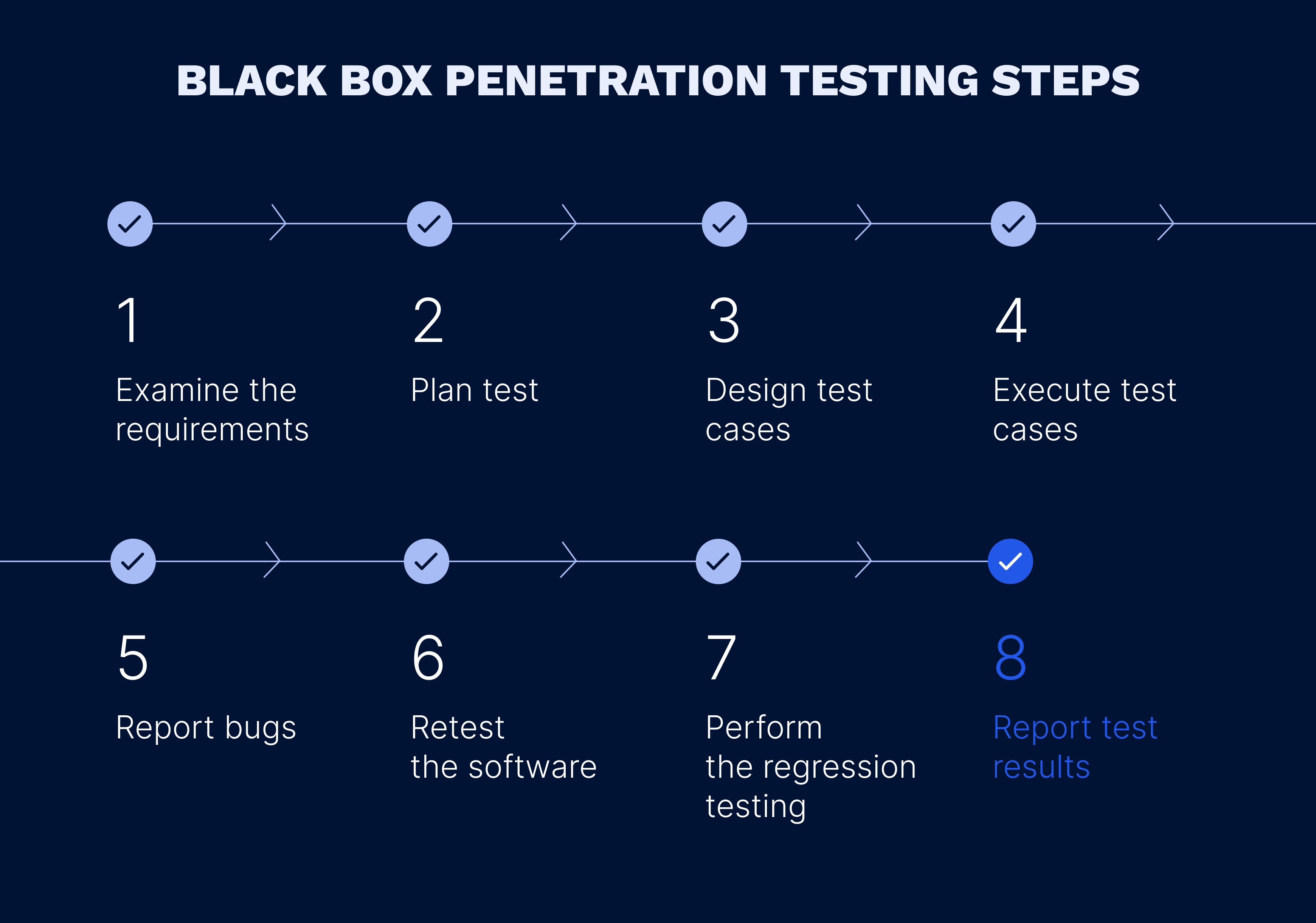
Knowing the basics of the black box pen testing, the next step to uncover is how to perform it. To successfully carry out black box testing, do as follows:
To automate the process by helping testers generate test cases, there are various software tools. Among them, the most popular are Selenium, Appium, Ranorex, UFT, AutoHotkey, Microsoft Coded UI, OWASP ZAP, Squish GUI Test Automation, and SilkTest.

The use of this methodology cannot solve all problems. Due to the lack of all-encompassing information about the software tested, the drawbacks are the uncertainty that the whole system has been examined and that security is strong. Black box testing cannot guarantee that all bugs are fixed as the practice implies examining a limited number of cases.
In addition, since this methodology totally relies on the experience of performers and is based on guesswork and trials, it carries risks tied to the human factor.
When implementing this methodology, specifications must be clear. The requirements must be set in a detailed and comprehensive way. Otherwise, it is impossible to create and conduct effective test scenarios, and therefore, successfully perform quality assurance.
The black box methodology is beneficial for various types of testing and provides its own unique advantages. It is suitable to fix flaws in the user interface or in the requirement specifications and ensures that all functions work properly. The most important feature of the black box approach is the close resemblance to hackers’ behavior, which helps to predict and prevent an attack.
Nevertheless, it is necessary to keep in mind that some errors, such as bugs in the internal code, cannot be found using only this method. Hence, to implement the most comprehensive verification, the best option is to use several types of pen testing simultaneously. To do this, make sure to delegate this task to reliable and expert testers.
At EffectiveSoft, we have built a robust Quality Assurance team to provide our clients with professional support for software testing. If you want a project estimate, don’t hesitate to contact us.
Our team would love to hear from you.
Fill out the form, and we’ve got you covered.
What happens next?
San Diego, California
4445 Eastgate Mall, Suite 200
92121, 1-800-288-9659
San Francisco, California
50 California St #1500
94111, 1-800-288-9659
Pittsburgh, Pennsylvania
One Oxford Centre, 500 Grant St Suite 2900
15219, 1-800-288-9659
Durham, North Carolina
RTP Meridian, 2530 Meridian Pkwy Suite 300
27713, 1-800-288-9659
San Jose, Costa Rica
C. 118B, Trejos Montealegre
10203, 1-800-288-9659